When you combine the estimates of multiple fraud control associations, annual fraud losses cost telecoms about $28 billion a year. And that doesn’t even count the huge losses enterprises suffer from these fraud attacks.
Of course, the methods fraudsters use to commit these frauds are in constant flux. As telecom operators year-after-year improve their ability to stop one kind of fraud, the fraudsters create new schemes and new ways to steal money and avoid detection.

One clever fraud that’s now frustrating even the most skilled fraud fighting teams is something called Call Stretching fraud, enabled when a normal international phone call is “hijacked” by a transit carrier.
AB Handshake Corp. is an expert in voice fraud detection and blocking and the company’s Managing Director, Vasily Birulin, is here to discuss Call Stretching Fraud and what service providers can do to remedy the problem.
Q. Why are operators having trouble detecting Call Stretching fraud? Can’t they use their Fraud Management Systems (FMS) to find and block it?
Vasily Birulin: The challenge in detecting Call Stretching is that the fraud hides inside legitimate international phone calls.
Fraud systems were designed to analyze call patterns in International Revenue Share Fraud. They detect calls involving illegal routing, call generation, common patterns that are seen in a massive amount of calls.
However, with Call Stretching, the call connection and initial conversation are legitimate, but the ending of call is fraudulent. So traditional FMS systems are simply not equipped to pick up this fraud at all.
Fraud scenarios that can be detected by a traditional FMS rely on typical call patterns – unusual destinations, low ASR and ACD, massive amounts of simultaneous calls to and from certain ranges. It’s a bird’s-eye view detection, so to speak. Of course, single fraud calls are ousted as well, especially if the use call details were previously seen in fraud cases.
An FMS uses analytics, volume thresholds, and AI/historical data to pinpoint the fraudulent calls sent, say, to “premium rate” countries like Cuba, where termination per-minute rates are very high.
Call Stretching doesn’t fit in these detection models because the fraud hides in legitimate phone calls, so detecting the fraud is bit like trying to find a “needle-in-a-haystack”. The fraudsters can inject this fraud across millions of phone calls and keep per-call profit small enough to stay “below the radar” of detection.
With Call Stretching, it’s the perfectly legal calls that are abused.
Q. How does the Call Stretching Fraud scheme work?
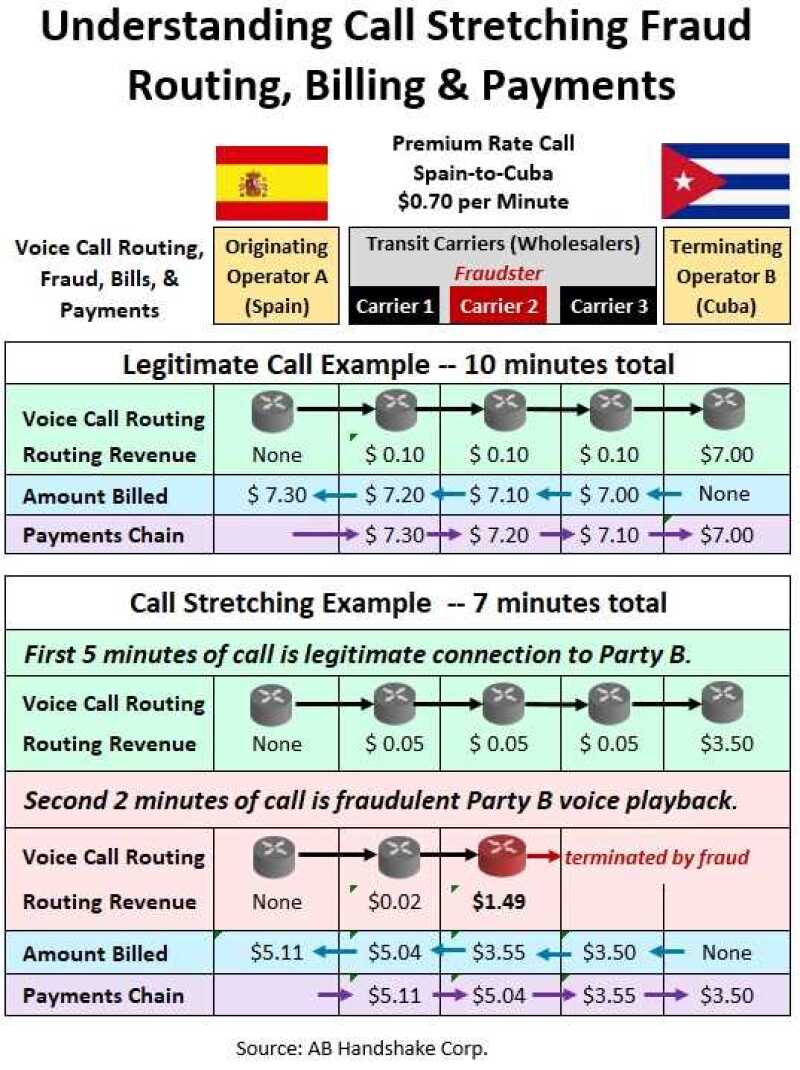
Vasily Birulin: Call Stretching Fraud actually begins with a simple phone call from Party A to Party B. And this is usually an international call that goes through a number of carriers. (See the diagram below.)
Let’s say the call originates in Spain and terminates in Cuba, a high premium rate country charging $0.70 (70 cents) per minute.
To better understand the fraud scheme, let’s compare it to the process of connecting and charging for a legitimate phone call.
In the legitimate call example, the three wholesale transit carriers each collect, let’s say, one cent per minute to connect and the Cuban operator (B Operator) eventually charges $7.00 for a 10-minute call. As you’d expect, each carrier bills the next carrier in the routing chain till you get to the A Operator who pays the full amount of the call’s cost.
Now let’s shift to the call stretching fraud,which also begins as a legitimate call from Party A to Party B, a call lasting five minutes, and for which the Cuban operator earns $3.50.
However, at the five-minute mark, transit Carrier 2 (the Fraudster) disconnects the call to Party B in Cuba, while simultaneously keeping Party A connected on the call. And the Fraudster substitutes the real voice of Party B with either the pre-recorded voice of Party B, or some other recorded content. (NOTE: Playing back the recorded voices of Party B is a serious privacy violation, by its nature.)
The whole purpose of the recordings and playback is to make the calling parties believe they are still talking to the B Party. As an example, to maintain that illusion, the fraudster’s recording might ask the caller to remain on hold while the called party is answering another call. A wide variety of recordings can be used.
So from the five-minute point of the call onward, Carrier 2 will bill for all the excessive seconds or minutes that Party A remains connected and doesn’t hang up. And the bill Carrier 2 sends for the remainder of the call is billed at the rate the Cuban operator is charging – $0.70 (70 cents) per minute.
Remember, Operator A has no idea that the call was disconnected to Operator B – and both operators are in the dark about the fraud taking place.
So as you can see, Call Stretching is a “smart” and highly profitable fraud scheme that current FMS’s and databases are not equipped to discover and block in real-time.
Q. So what can be done to block Call Stretching?
Vasily Birulin: The answer to this type of fraud is to establish a fast, private and secure network link between the originating and terminating operators to be able to instantly check the call integrity. It shouldn’t reveal the connection status: it only has to notify about the status changes.
And that’s the purpose of the AB Handshake system. It enables the A and B operators to communicate with each other via direct secure out-of-band connection. The diagram illustrates how AB Handshake handles Call Stretching.

Call Stretching Fraud – In the Call Stretching fraud scheme, the call is made to any active phone number and in the beginning portion of call, the A and B Parties are legitimately connected and having a normal conversation.
But shortly thereafter, a transit carrier Fraudster breaks/finishes the call to Operator B while keeping the Party A from hanging up by playing a pre-recorded conversation or other content to make Party A believe he's still connected with Party B.
Now since Operators A and B are both connected to the AB Handshake Call Registry, when the fraudster terminates the call to Operator B, the Handshake B Registry automatically alerts the Handshake A Registry that the connection on the B side has ended.
By this, Operator B immediately informs Operator A that it must close the Party A call to prevent possible call hijacking.
So in both displayed cases, a real-time out-of-band exchange of the call information between Operator A and B enables full visibility and control over the fraud problem even without any intervention of an FMS. And since Handshake call registries of Operator A and Operator B communicate directly over the secure encrypted channel, no intermediaries can affect the call validation process, so the AB Handshake call validation procedure becomes a genuine source of information about the call status.
It’s interesting that AB Handshake Corp., whose industry pros come from the wholesale side of telecom, has built a solution to solve the fraud problems that mostly concerning retail service providers.
Vasily Birulin: In fact, trustworthy wholesalers have a keen interest in seeing fraud eliminated. They know how much pain fraud causes. It’s a major industry headache that leads to customer frustration, revenue losses, costly disputes, and damaging business relationships. So both sides – retailers and wholesalers – have a strong commercial stake in seeing a cost effective solution to counter the fraud.
And, as I’ve explained, the rise in Call Stretching introduces a fraud scheme that cannot be solved by traditional FMS systems. So we thought: 'Why not give it a go and launch the system that will use a community-based paradigm of combating the fraud?' Considering it’s a very low investment on operator side, at the same time it has potential to bring a serious gain on the revenue side.
Of course, the initiative first needs industry-wide acceptance by the community of anti-fraud professionals. Actually we have been spreading the word about AB Handshake for about a year till now, we first introduced it at an i3forum wholesaler conference in Miami.
It was at that event, when we met the head of fraud control at a Tier 1 mobile carrier: He loved the concept and said he wants to see it implemented everywhere in his organization. But the transit operators in the room asked him the question: "We are wholesale carriers, so how can we benefit from this?"
His answer was simple yet prominent: “Once the system is installed, there will be no fraud at all. So wholesalers will certainly benefit too.”
Now it certainly takes some time between idea inception and the real system implementation. But from beginning, the big operators are on our side. So now we are doing the next steps - integration of our solution with operator networks and connecting them to the AB Handshake community.
Of course, the real power of AB Handshake comes from the sheer number of operators that use it. Sure, a traditional FMS brand would enormously benefit from a Tier 1 operator using it, but with AB Handshake it’s about the volumes of traffic validated by the system, not as much about the names.
So this brings us to a very consistent message when we introduce AB Handshake to new parties – most important is not who exactly is using the system, but how many operators are on board and how much traffic is already validated, and what destinations are covered.
The concept of AB Handshake is very simple and we have already built a low-cost Call Validation Registry and out-of-band communication network that can be implemented at low – or at no – cost. It’s basically about getting the A and B operator to share intelligence with each other.
Today, AB Handshake is the only system in the world that can stop Call Stretching fraud, and I’m glad that we are coming with such a solution at the right time to help operators across the globe to counter this emerging type of fraud.





